Where Are You Most Likely To Find A Pkes System?
Where are you most likely to find a pkes system?. The PKES enables drivers to unlock and start their cars without user interaction. Where are you most likely to find high density. An infection would most likely increase phagocytic activity in Tissue interstitial fluid would most likely be found in.
It is a perfectly sunny day with no clouds. The peppers could be useful to run to different locations but youre only likely to get 3 or 4 apples at most from here. These can be apples or things like bananas or peppers.
Where are you most likely to find a PKES system. In which one of the following preparations are you likely to come across cell junctions most frequen. He told the group the focus now is likely to be on keeping less-sick patients out of the hospital or out of intensive care beds if that can be safely done.
Combining those theocracy stands for religious leadership and their states legal system is based on religious law. Where you are likely to find an embedded operating system. An automobile From January 2005 through July 2015 approximately how many electronic data records in the United States were breached exposing to a range of personal electronic data such as address Social Security numbers health records and.
Where was it most likely that the two girls would find work after school. OBJECTIVE1To prepare1-bromobutane2To find the percentage yieldcalculation of 1-bromobutane3To observe the boiling point and literature boiling point of1-bromobutane INTRODUCTION In this experimentnucleophilic substitutions are one of the most useful of synthetic organicreactions It introduces the class of reaction which is second ordernucleophilic substitution. Where are you most likely to find a PKES system.
At Catty Corner theres NOMS boxes scattered around. You are participating in a school debate on the topic Roles of advertising for the business societ. Where are you most likely to find a photoautotroph lives near the surfaces of lakes streams and oceans Answer Photoautotrophs are anything photosynthetic and thus must be found anywhere with sufficient sunlight.
Closing entries are journalized and posted. You are staying in Keystone Colorado at 9000 feet.
Where you are likely to find an embedded operating system.
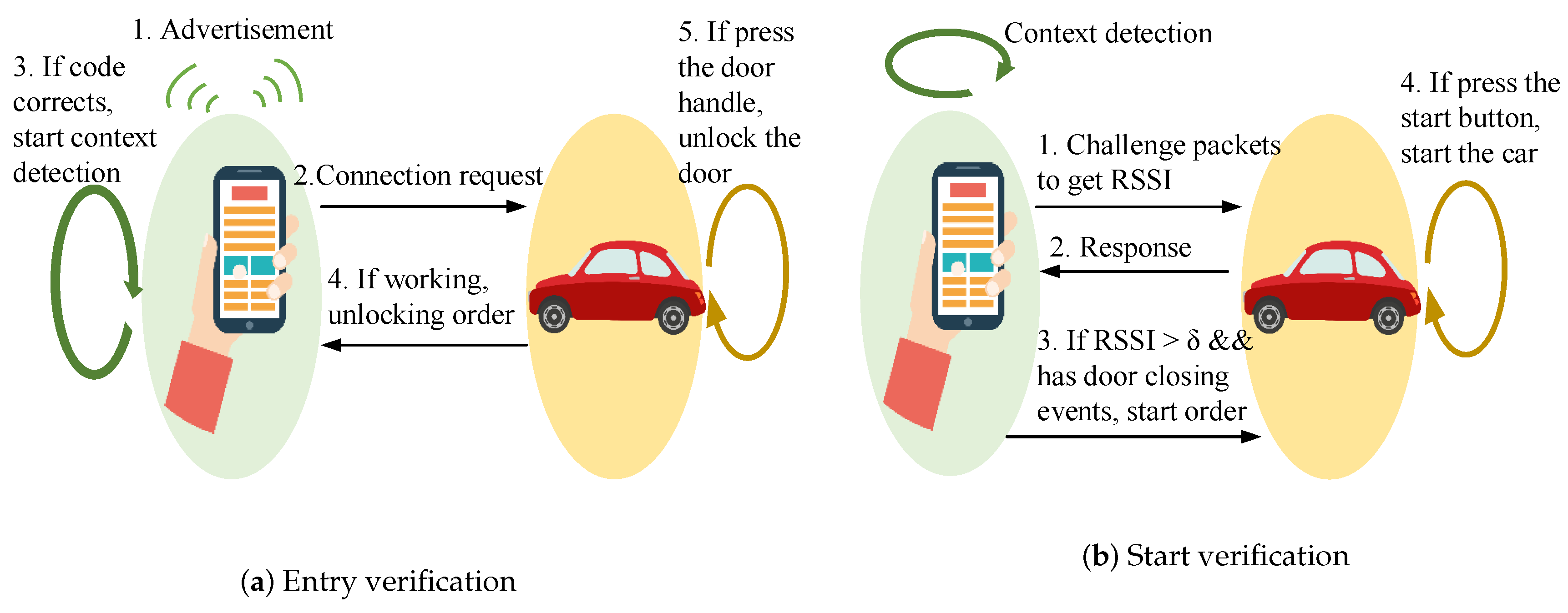
An infection would most likely increase phagocytic activity in Tissue interstitial fluid would most likely be found in. Integrity Which of the following ensures that information is correct and no unauthorized person or malicious software has altered it. When you go up to them and search them random fruits and vegetable will appear. In modern cars the Passive Keyless Entry and Start system PKES has been extensively installed. Cities where wearing clothes is not allowed August 13 2021. They are quite difficult to find so we recommend that you go to the oasis in the southern half of the desert not far from where the road crosses. OBJECTIVE1To prepare1-bromobutane2To find the percentage yieldcalculation of 1-bromobutane3To observe the boiling point and literature boiling point of1-bromobutane INTRODUCTION In this experimentnucleophilic substitutions are one of the most useful of synthetic organicreactions It introduces the class of reaction which is second ordernucleophilic substitution. He told the group the focus now is likely to be on keeping less-sick patients out of the hospital or out of intensive care beds if that can be safely done. If they dont appear around the oasis then run east along the river and you will likely see them on the edge.
Where are you most likely to find a pkes system. When you go up to them and search them random fruits and vegetable will appear. Closing entries are journalized and posted. Inside or outside of the car Francillon et al. Where was it most likely that the two girls would find work after school. Integrity Which of the following ensures that information is correct and no unauthorized person or malicious software has altered it. He told the group the focus now is likely to be on keeping less-sick patients out of the hospital or out of intensive care beds if that can be safely done.












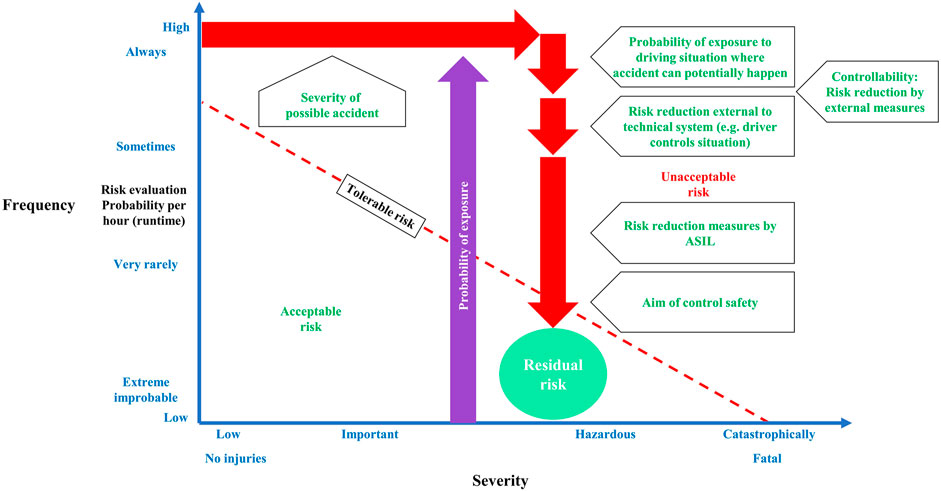



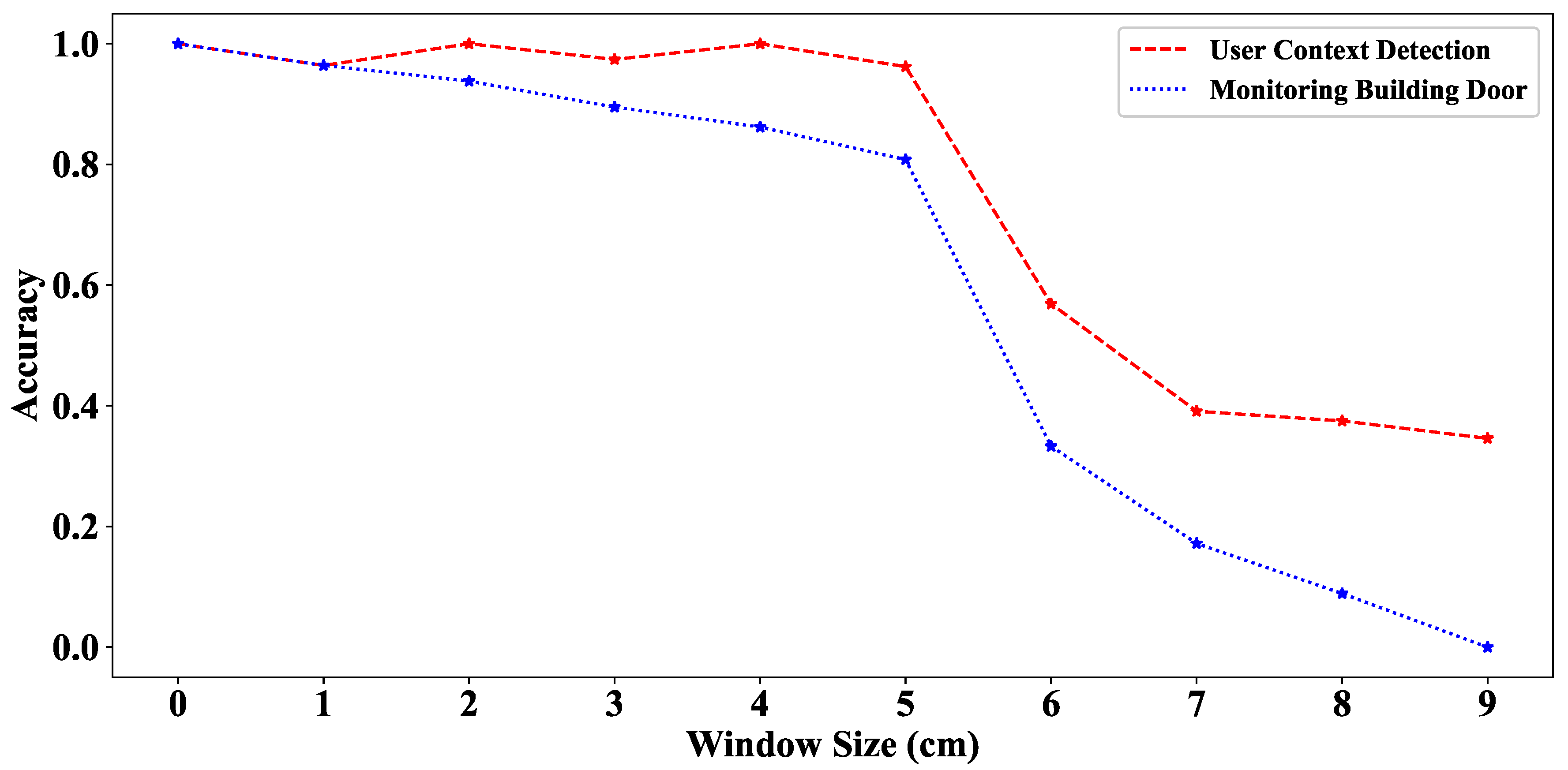
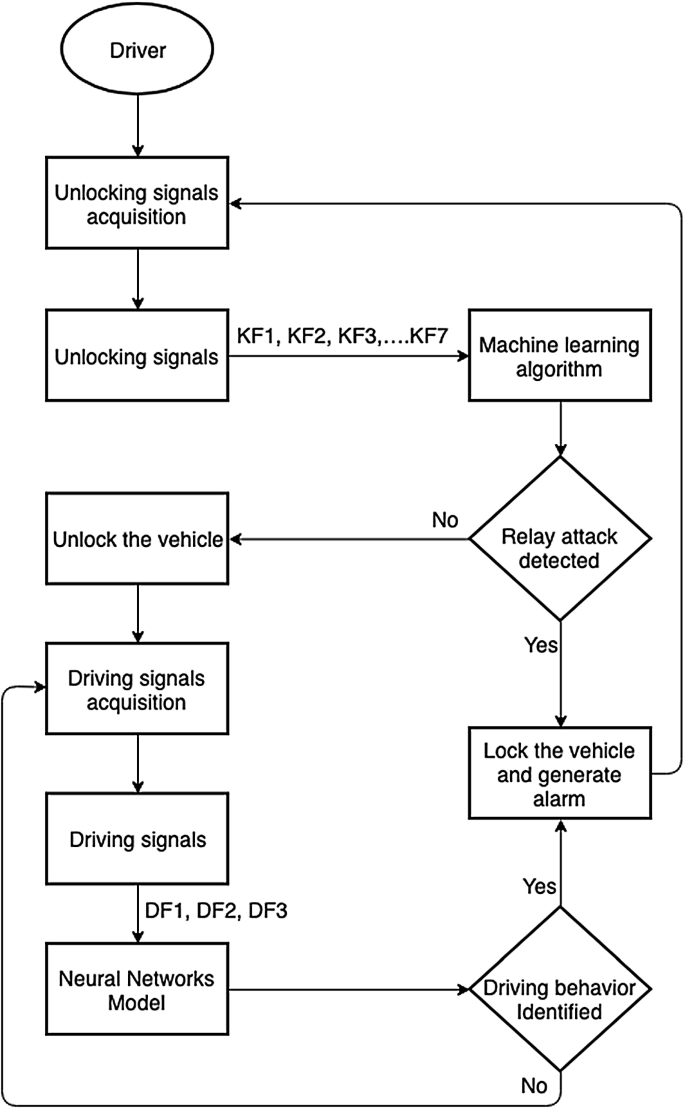
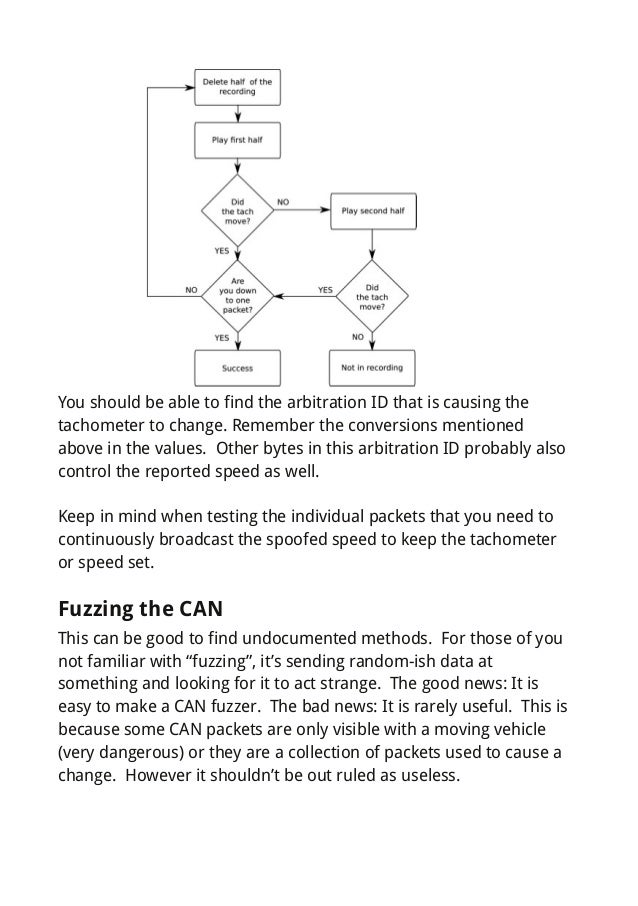











Post a Comment for "Where Are You Most Likely To Find A Pkes System?"